Block Bell's or Rogers's DNS hijacking (domainnotfound.ca)
Friday, July 31, 2009
Yesterday night, while surfing around, I noticed that when a domain name wasn't registered I was being redirected to a Bell search page, a page coming from domainnotfound.ca. If you haven't seen it, it looks like this:
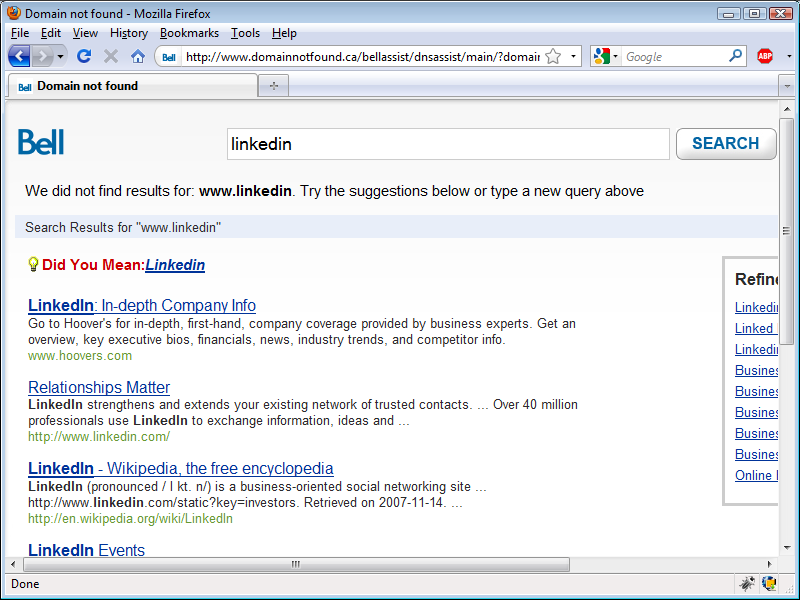
When I saw it, I thought my computer was infected with a virus. After looking around my computer for a few minutes, I figured out what was going on. Bell is hijacking invalid or non-existing DNS entries to display, likely, sponsored search results via their network. Note that I was trying to go to someone's LinkedIn profile and also note how this DNS hijacking process is now telling me that LinkedIn doesn't exist, when it clearly does.
I knew that Rogers already did this, but I don't use Rogers, so I've never seen it in action. But now that Bell is doing, I can see clearly that I don't like it.
First, Bell doesn't ask if you want to participate in this practice. Second, if there is any link sponsorship, I don't see any money coming my way. Third, I already pay for my internet service, so I don't think I should unwillingly become another source of revenue for Bell.
I'm not sure if anyone else out there cares that this traffic shaping happens. I'm not even sure if anyone has noticed. However, there is something you can do, and it's doesn't involve using OpenDNS--read their
privacy policy first: they can see everything you do and they say that they will sell that information (in fact, that's their business model).
An easier solution is to modify your
hosts file in your computer. Your
hosts file helps your computer connect to servers faster, by bypassing the process of DNS table look ups (if you don't know what this means, don't worry about it). So, modify your
hosts file to look like this:
# Copyright (c) 1993-2006 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
127.0.0.1 localhost
127.0.0.1 www.domainnotfound.ca
127.0.0.1 bellcanadaassist.infospace.com
127.0.0.1 assist.infospace.com
::1 localhost
The servers that you need to block are
www.domainnotfound.ca,
bellcanadaassist.infospace.com, and
assist.infospace.com.
Technically speaking, you are not really blocking them; what's happening is that whenever a request to either one of these severs is executed, it resolves the address to your machine (127.0.0.1).
Where is this magical
hosts file? In Vista is in
C:\Windows\System32\Drivers\etc.
Before modifying this file, make a backup of it. Then add these 3 lines to it:
127.0.0.1 www.domainnotfound.ca
127.0.0.1 bellcanadaassist.infospace.com
127.0.0.1 assist.infospace.com
Save the file, and that's it.
With this minor change, Bell can't hijack your mistakes. And don't bother with Bell's "opt-out" option: it still does the hijacking and the company knows that you made a mistake, but it doesn't do the search because a cookie is set to not go to the search page. In other words, opt-out is not really an opt-out option.
If you are a Rogers user, you'll need to figure out which servers are doing the DNS hijacking, but the solution is the same.
Labels: Bell DNS, DNS hijacking